Anomalix Enables Security and Governance for ServiceNow Provisioning and Integration
Audit and Compliance
Often times organizations are spending too much time (and valuable resource allocation) to produce audit reports that demonstrate compliance of who has access to what, how that access was requested and approved, and when that access was granted. This effort is typically cross-organizational and spans IT and the Lines of Business. While many organizations rely on ServiceNow for requests and approvals, the Identity Management system is leveraged to automate the fulfillment of access changes. Anomalix has enabled organizations to leverage their ServiceNow investment to integrate with the Identity Management system of choice for efficiency and automation and cost reduction for daily operations as well as audit and compliance purposes. ServiceNow Identity Management integration has tremendous value for any organization that is looking to automate services and reduce costs associated with service request fulfillment and compliance reporting.
Traversing the Last Mile
ServiceNow is a leader in the access request, incident management, and IT ticketing space. While it provides extensive capabilities around the generation and management of user access requests, completing the last-mile of automated provisioning can be challenging for organizations of all sizes. Anomalix can enable businesses to close the gap of last-mile fulfillment through the configuration and customization of ServiceNow & Identity Management System integrations.
Reining in User Access Requests
End-user access requests have been traditionally challenging at the enterprise level. Large organizations will typically have multiple, disparate processes for requesting access. These include re-purposed IT asset ticketing systems, homegrown solutions, group email inboxes, and calls to individual administrators. The result is user confusion, difficulty or inability fulfilling compliance requirements, and inefficient and costly maintenance processes.
ServiceNow IT Service Management aims to bring a service-based approach to IT access requests. The result of a fully realized implementation is reduced IT management costs, increased user satisfaction, and easier fulfillment of audit and compliance requirements. Coupled with the automated fulfillment capabilities found in Identity and Access Management Systems, this becomes a powerful solution for end-to-end user lifecycle management. Additionally, requests generated in the Identity Management System can point to ServiceNow to generated tickets for manual fulfillment.
Configured Your Way
Anomalix knows that each organization has unique requirements for ServiceNow Identity Management integration. Business specific use cases around end-user access requests, audit and compliance mandates. We have experience with ITSM, Identity Management, as well as IT Audit and Compliance. Anomalix has integrated Identity Management systems with ServiceNow both as the generator and receiver of fulfillment requests. Furthermore, these patterns are not mutually exclusive; hybrid implementations are possible that allow ServiceNow to generate fulfillment requests and act as a fulfillment endpoint, should the need arise.
Figure1: Identity Management Fulfillment
The first pattern represents ServiceNow utilizing the Identity Management Integration to fulfill requests. This allows organizations to leverage existing provisioning connectors to automatically fulfill access requests.
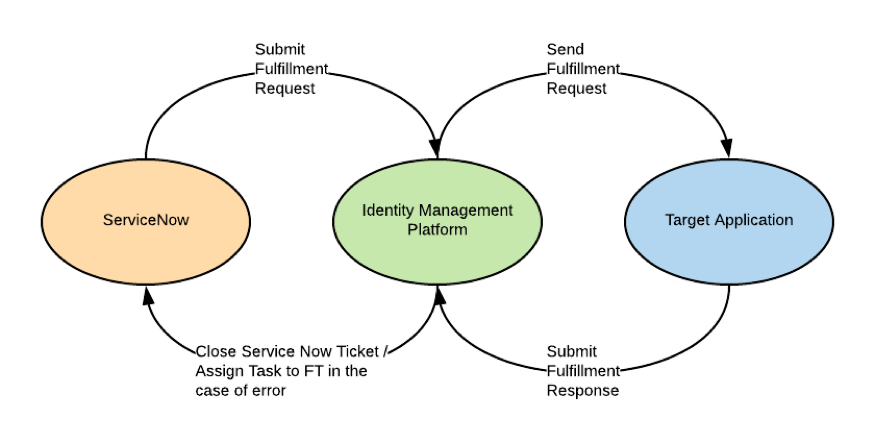
Figure 2: ServiceNow Fulfillment
The second pattern demonstrates ServiceNow Identity Management Integration where ServiceNow is acting as a fulfillment endpoint for requests generated in the Identity Management System. Systems that are not integrated or rely on ServiceNow tickets for fulfillment can still leverage request generated (manually or automatically). Proprietary workflow capabilities can monitor the status of the ticket and close the request when it has been marked complete in ServiceNow.

Planning for Success
High-level planning for how your company can leverage ServiceNow and your Identity Management System is a fairly straightforward affair. It comes down to answering four key questions:
- Which system will be used to create access requests?
- Which system will be used to approve access requests?
- Which system will be used to fulfill access requests?
- Which systems are the authoritative source of truth for audit and compliance?
Anomalix professional services can help plan, implement, and support your organization’s needs in each scenario.
Anomalix On-Premise and Cloud Identity Management Services
- Identity Lifecycle Management experience with packaged application integrations including Office 365, ServiceNow, SAP, Cerner, Epic, Google Apps, Workday, Azure Apps, Oracle ERP, AWS Apps, and PeopleSoft
- Proven success in large, complex heterogeneous enterprise environments (On-Premise and Cloud) where internal processes and procedures are immature or non-existent
- Audit & Compliance remediation experience to solve best practice deficiencies and satisfy regulatory mandates
- Experience in migrating from legacy Identity & Access Management (IAM) systems to modern IAM solutions
- In-house Project Management capabilities
- Data Analytics experience analyzing and parsing data to provide actionable analytics options for customers
- Anomalix boasts 98% Client Satisfaction, with a 92% rate of repeat business
- Anomalix Team has decades of experience in delivering Identity Management solutions
- Anomalix leverages a proprietary Design and Delivery process
Mohammed Elkhatib is Founder and CEO at Anomalix. Prior to founding Anomalix, Mohammed led global operations for Aveksa (acquired by RSA) where he was responsible for Sales, PreSales, Engineering and Professional Services. Mohammed is an Identity Security expert with over 25 years of IT and Business experience.



